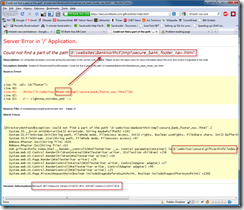
Hmmm…Saturday before Christmas here in the U.S. of A., major banking site, error page like this:
I’ve been developing in ASP.NET since 2002 so I think I can safely say that somebody screwed up and they’ve got some sloppy practices in place!
Looks like ‘Banknorthct’ is a valid #bankid# token in case you’re trying to discover information about their site. Also, they like to use D:\websites to store their site files in so hackers shouldn’t have to go hunting for that configuration detail. Finally, they’re running .NET 2.0 which means it’s a lot easier for folks to attack because they can immediately try all known exploits.
Do I seem too harsh? Well, two simple steps would’ve prevented this:
- Turn ‘RemoteOnly’ back on in your web.config – someone explicitly changed it from the default value.
- Code a custom error page possibly with a redirect so the customer doesn’t see your dirty underwear!!
Tell me again how much banks got for a bailout in ‘09 and ‘08 and how much profit are they raking in now?
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.